The consequence of traditional perimeter security protection is finding threats only at the fence line when it’s too late. Nonetheless, the leading approach to securing a facility is by surrounding it with a fence. There’s a reason we don’t use moats around castles anymore.
Yet we still protect our facilities with fences, cameras, and access control systems, a growing market valued at $37.43 billion by 2021. With this traditional approach, many long-standing protection challenges still exist even with additional spending.
For real-world threats it’s critical to see beyond your walls and cameras to detect and track threats early before reaching the fence line and after they get past. When you secure your home at night, do you just lock your bedroom door?
 Don’t wait until a threat is at your door. Expand your perimeter security with invisible ground sensors.
Don’t wait until a threat is at your door. Expand your perimeter security with invisible ground sensors.
Concentrating all of your security options at a wall, fence, or physical perimeter is proving to be dangerous for many organizations.
Your perimeter is your last line of defense but being aware of what happens in the area beyond that has been difficult to achieve. That’s why modern security strategies are not just built around containing known threats but monitoring activity early on to provide advance warning and tracking information to security response teams.
Where do ground sensors fit into this concept?
As cyber-attacks become a regular occurrence and the risk of physical attacks increases each year, security professionals are looking for new ways to develop an earlier detection of threats.
The commercial market now has access to the tools and systems that make this possible. For physical security protection, a new generation of footstep sensors has been designed to provide a better understanding of what threats are doing both inside and outside your perimeter.
Each scenario for implementing a security solution is site-specific. A prepared private citizen addresses trespasser differently than a substation security officer, or how a border patrol agent would choose to interdict threats. With so many possibilities for how security can be implemented, let’s look at the range of applications where a footstep detection system can play a role.
Modern intrusion detection systems have been developed specifically to support common security scenarios by focusing on three emplacement objectives:
- Perimeter & Border Security
- Surveillance Detection
- Threat Pattern Analysis
Each objective can begin as a very simple deployment and expand to a sophisticated multi-layered strategy. Let’s look at some examples of how this newest generation of footstep detection systems is improving security.
1. Perimeter & Border Security
Attacks or intrusions are most commonly preceded by some level of surveillance or reconnaissance. If you have an established perimeter or virtual fence that is not well concealed, a threat can easily identify and avoid it. If an intruder knows where to look, then they’ve already won.
Footstep detection sensors used correctly can combat this problem by monitoring activity in the right spaces, instead of the entire protected area.
Place sensors near a facility to secure the surrounding perimeter or selectively in known vulnerability points to provide an advance warning of threat activity. It’s not always necessary or feasible to entirely surround your facility, and using sensors designed with that in mind allow you to be as effective as possible.
Designed to be covert in several ways, modern ground sensors buried just below the surface make it extremely challenging for threats conducting surveillance or site incursions to locate them. Users can make it even more covert and difficult to detect when an asymmetrical emplacement approach is used. This is contrary to traditional perimeter security methods which use sensors emplaced linearly, making them easy to identify and once beyond the sensor line the adversary is free to travel anywhere inside the perimeter without detection.
Asymmetric sensor emplacement allows you to focus on known vulnerability points, not the entire perimeter, even if they are close to your facility. Positioning them in a “dead space” that isn’t otherwise monitored by cameras or personnel provides a needed advantage in a layered defense approach.
Even if your facility or surrounding landscape necessitates a linear approach, these next generation of ground sensors will support your frontline defense and monitor any blind spots for cameras.
Examples of common perimeter and border-related security users include but are not limited to:
- Ranchers
- Private landowners
- Timber companies
For security professionals operating in remote areas or with limited budgets, an asymmetrical buried ground sensor layout \ allows them to monitor activity effectively with or without integrating into a larger security infrastructure. Receiving better detection information with fewer sensors and at a lower cost makes good economic sense.
2. Surveillance Detection
Monitoring threats as they perform reconnaissance in your protected area is necessary in many situations. Surveillance detection is often hard to do, especially in remote areas or harsh landscapes with many line-of-sight obstacles. Therefore, having a standalone solution that is capable of surveillance detection is essential for many security professionals and organizations.
Footstep detection sensors that are deliberately emplaced with surveillance detection in mind can determine how threats are using routes into and out of your protected areas. Expanding your use of sensors progressively farther out from your perimeter allows you to gain the unique opportunity to find out more information on how and when you are being surveilled.
Apply sensors to routes, corridors, key locations, and even camera “blind spots” to map movement during surveillance. Increasing your standoff capability beyond a perimeter provides security professionals with an extended amount of time to react or prepare their response.
For many this approach results in a more economical security solution. Intelligent dispersion of sensors requires fewer sensors with the same or better protection. Use data and insight from past activity and strategically place sensors in areas where surveillance has or can occur, instead of completely surrounding your facility.
Surveillance detection users include but are not limited to:
- Large corporations
- Critical infrastructure firms and utility providers
- Integrated security teams
- Military
- Border Security Agencies
3. Threat Pattern Analysis
A complete understanding of all activity beyond your perimeter is the end goal in many physical security situations. Performing surveillance detection does help accomplish this, but only provides information on threats once they are actively surveilling you.
Understanding threat movements and patterns before surveillance occurs allows security providers to have an even earlier warning of threats.
In some situations, the risk of not having as much information as possible is too great. In others, the surrounding landscape and natural “blind spots” dictate the need for detection well before surveillance can occur.
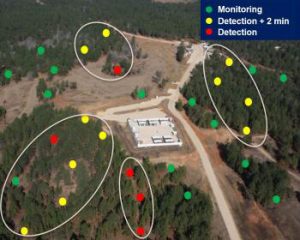 It’s critical to first gain an understanding of the pattern of normal behavior within an area. To establish baseline patterns and identify anomalies, footstep detection sensors are strategically placed far from your perimeter, providing you with a greater understanding of what normal activity looks like.
It’s critical to first gain an understanding of the pattern of normal behavior within an area. To establish baseline patterns and identify anomalies, footstep detection sensors are strategically placed far from your perimeter, providing you with a greater understanding of what normal activity looks like.
This information is collected over weeks or months to provide an activity baseline. That is then analyzed together with your data on threats, which allows you to identify anomalies. Graduate your emplacement of sensors further away based on these anomalies to determine how threats are moving to their surveillance locations.
A benefit of this approach is that you can choose when and where to interdict the threat so it looks like a chance encounter. You can thereby avoid disclosing the location of your ground sensors and continue with future threat surveillance.
This evolving and asymmetric approach using footstep detection sensors is disrupting how security professionals view traditional perimeter security. It’s a proactive alternative to monitoring threats, compared to the reactive approaches we continue to use today.
Rethinking Past Approaches
In applications where a virtual fence around an entire perimeter is being considered, a better approach would be to focus ground sensor emplacement on known vulnerability points. A footstep detection system like Pathfinder can be used asymmetrically to protect that same perimeter, using fewer sensors at a lower cost and gaining an earlier warning of activity.
Pathfinder was specifically designed to help security professionals identify patterns of threat behavior through a progressive placement approach. Start by focusing on a few areas at your perimeter and begin extending your coverage further away to gather a more complete understanding of activity.
With Pathfinder you not only get an undetectable security solution with an improved footstep detection capability, but also the ability to improve your threat assessment and shorten your critical response time.
How do I learn more about Pathfinder?
It’s easy, just set up a consultation with our security experts. Applied Research Associates is uniquely qualified to help your organization execute a sound security and emplacement strategy using the Pathfinder system.
Pathfinder Protects Borders With:
- Extended battery life (MINI sensor: up to 6 months; XL sensor: up to 24 months)
- Focused detection radii and point detection capability
- Long range detection reporting without the use of gateways and relays
- Signal exfiltration in line of sight, non-line of sight and beyond line of sight conditions
- Intelligent, machine learning algorithms
- High probability of detection and low false alarm rate
- Static and mobile detection receipt and monitoring
- Ruggedized sensor capable of withstanding a wide range of climates and terrains
Compromise and Defeat Protection
- Waiting until the threat gets to the wall or beyond the wall is too late. Know where the threat intends to breech the wall/fence and monitor their approach long before they ever get there
- Protect existing infrastructure by automatically cueing existing cameras, radars, drones, etc. to positively ID threats and initiate the appropriate response inside, at, and beyond standoff distances from the threat

