3 Common Perimeter Security Mistakes
Perimeter security is a vital part of any physical security plan to prevent intrusions and keeping your facility safe from all angles. It comes in various forms, from cameras to fences to ground sensors, all of which can play an essential role in protecting your facility from unwanted outsiders. Unfortunately, it’s not uncommon for security personnel to ineffectively employ some perimeter security components like buried ground sensors.
In today’s article, we’ll discuss three common perimeter security mistakes usually associated with ground sensor emplacement and how you can overcome them to optimize your facility’s perimeter security threat protection levels.
Perimeter Security Mistake Number One: Linear Sensor Placement
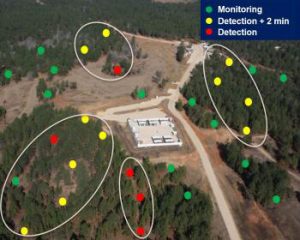
First, I would like to clarify that linear ground sensor emplacement is not always a “mistake.” It can be a viable, successful way to keep your facilities secure by creating an “invisible fence” around your facility like the picture below.
 This is a commonly used tactic and is excellent for identifying when something or someone is entering your property, but it can also have several dire drawbacks.
This is a commonly used tactic and is excellent for identifying when something or someone is entering your property, but it can also have several dire drawbacks.
The first of which is that linear ground sensor emplacement offers little information about who or what is trying to enter your property as well as their intent once they have entered your grounds.
Using daisy chain placement only informs you that something or someone has crossed the threshold of your perimeter. After that, you have little to no information about where they have come from, where they go, or when they leave.
Most often, linear ground sensor emplacements are employed right along the defended area, resulting in security personnel only being alerted once the intruder has successfully crossed onto your site.
In these situations, the intruder may be able to damage your facility or burglarize assets before your staff has time to intercept the threat.
Another issue with linear sensor emplacement is its tendency to cost more money than needed by securing the whole space but not necessarily the right space.
Virtual fencing requires sensor emplacement around an entire facility, which means you’ll have to purchase more sensors than if you were to adopt a strategic emplacement approach. To ensure personnel has enough time to react after receiving an alert, you must push your linear fence out even further from your facility, requiring even more sensors.
With commercial sensors ranging in price from $500 to more than $3,500 apiece, the cost of linear perimeter security can quickly spiral out of control.
Our Solution:
We recommend strategic perimeter security sensor emplacement in addition to, or instead of, linear sensor emplacement.
By placing your security measures in strategic points of penetration, such as bridges, gates, fence lines, and rail lines, you’re able to secure the most probable entry points without having to blow your budget to secure your entire space.
Ground sensor emplacement beyond your perimeter will also notify personnel of any suspicious movement approaching the facility, giving them a chance to monitor and intercept the threat before its able to cause any harm.
Perimeter Security Mistake Number Two: The Reactive Approach
Security personnel often take a reactive instead of a proactive approach to perimeter security, in which they wait for an alarm to sound and then act without monitoring the situation.
Like linear ground sensor emplacement, a reactive approach to security also limits your staff’s ability to analyze and intercept the threat before they’re able to cause harm.
Our Solution:
We recommend a proactive approach called threat pattern analysis that allows you to, over time, understand normal behaviors within and around your facility’s grounds.
You can do this by strategically emplacing unattended ground sensors outside of your perimeter, which will help you identify and understand regularly occurring behavior patterns and those that are out of the ordinary.
Once you can create a baseline of normal behavior over weeks or months, you can compare your findings to data from previous threatening situations, allowing you to identify anomalies.
After this process is complete, you can emplace additional ground sensors even further beyond your perimeter to gain insight into how threats conduct surveillance that often precedes penetration attempts.
The purpose of collecting historical movement patterns is to provide security personnel with a more in-depth understanding of how future threats will surveil and approach your facility. These insights will enable them to monitor and identify threats before perimeter penetration attempts.
Knowing movement patterns will also help you to choose when and where you’ll be able to intercept the threat, creating the perception of a “chance encounter” without disclosing your ground sensor emplacement locations, strategy, and overall perimeter security capability.
Mistake Number Three: Only Employing Visible Security Measures
Many companies employ visible security measures, such as cameras and fences, to deter intruders. While we support the use of these security measures, attacks or physical penetrations are almost always preceded by some surveillance or reconnaissance level.
In other words, visible security placement enables intruders to study your perimeter security layout and devise a plan to avoid or destroy visible security equipment long before an attack.
Our Solution:
Covert ground sensors are a great alternative, or partner, to visible security measures. Ground sensors are designed to sit just below the surface, making them a covert security measure that will likely go unnoticed by threats surveilling the area.
For optimal protection, ground sensors can be placed asymmetrically around your facility, making it even harder for intruders to understand your perimeter security layout.
As we mentioned earlier, linear ground sensor emplacement may allow intruders to predict your security zones’ placement, allowing them to devise a plan to avoid or damage them.
With a sporadic yet strategic ground sensor emplacement plan, ground sensors can allow you to secretly monitor, analyze, and intercept your threat in advance of penetration or while the intruders are on your property, knowing exactly where they are headed.
By sending your security team to their location, you will be able to keep the intruders moving instead of having the time to burglarize, steal, or damage property or possessions.
Overcoming the Issues with Perimeter Security
The best way to overcome weaknesses in your overall perimeter security plan is to implement an integrated security setup that diversifies your security measures to overcome any site-specific perimeter security plan’s inevitable vulnerabilities.
Pathfinder ground sensors work well with Perimeter Security security cameras and fences to give a well-rounded security solution that will help you overcome weaknesses in your current perimeter security layout.
Pathfinder ground sensors provide a completely stealthy alternative to traditional perimeter security with the ability to send alerts to your cell phone when movement is detected.
Our employees are trained in the underground sensors’ strategic deployment to help you identify the most advantageous positioning of the sensors to ensure the most effective and affordable perimeter security layout.
Contact us today to see how we can help you secure your perimeter with Pathfinder ground sensors.
Pathfinder Protects Borders With:
- Extended battery life (MINI sensor: up to 6 months; XL sensor: up to 24 months)
- Focused detection radii and point detection capability
- Long range detection reporting without the use of gateways and relays
- Signal exfiltration in line of sight, non-line of sight and beyond line of sight conditions
- Intelligent, machine learning algorithms
- High probability of detection and low false alarm rate
- Static and mobile detection receipt and monitoring
- Ruggedized sensor capable of withstanding a wide range of climates and terrains
Compromise and Defeat Protection
- Waiting until the threat gets to the wall or beyond the wall is too late. Know where the threat intends to breech the wall/fence and monitor their approach long before they ever get there
- Protect existing infrastructure by automatically cueing existing cameras, radars, drones, etc. to positively ID threats and initiate the appropriate response inside, at, and beyond standoff distances from the threat

